Your vendors now trigger nearly a third of data breaches. Verizon’s 2024 DBIR reveals that 15% of breaches involved a third party, a 68% increase from the previous year. Effective third-party risk management has shifted from a compliance checkbox to a front-line security necessity as supply-chain attacks continue to escalate.
With many organizations now relying on centralized recovery management to safeguard critical data, the stakes have never been higher. SecurityScorecard reports that 98% of companies work with at least one vendor breached in the past two years. The 2023 MOVEit zero-day alone affected more than 2,700 organizations and exposed the data of over 95 million individuals, proving that a single vendor flaw can cause systemic global damage.
Regulators noticed. The SEC’s four-day disclosure rule and Europe’s upcoming NIS2 and DORA now require continuous third-party oversight.
Key Takeaways
- Third-party risk management is essential due to the rising number of breaches involving vendors, represented by a 68% increase from last year.
- Verizon’s report shows third parties account for 30% of breaches, necessitating continuous oversight and compliance checks by regulators.
- Effective TPRM tools should automate assessments, enable continuous risk monitoring, and facilitate real-time compliance tracking across multiple frameworks.
- Top solutions like Vanta, OneTrust, and SecurityScorecard excel at specific functionalities, catering to various organizational sizes and needs.
- Implementing a focused pilot program and assigning clear roles helps organizations maximize the benefits of third-party risk management software.
Table of Contents
- Why Third-Party Breaches Deserve Front-Page Attention
- How We Picked the Third-Party Risk Management Software Winners
- Key Buying-Factor Checklist for Third-Party Risk Management Software
- Top 5 Picks for Third-Party Risk Management Software
- 1. Vanta: Best for Automated Compliance and Vendor Trust
- 2. OneTrust: Best for Enterprise Vendor Risk and Privacy
- 3. SecurityScorecard: Best for Continuous Cyber-risk Visibility
- 4. UpGuard: Best Mid-Market All-Rounder with AI-assisted Workflows
- 5. Prevalent: Best for Shared Assessment Libraries and Due-Diligence Speed
- Side-by-Side Snapshot
- Which Tool Fits Your Program?
- Implementation Tips and Next Steps
- Conclusion
- FAQ
This guide ranks the five TPRM platforms that help you stay compliant and protect your business—without drowning in spreadsheets.
Why Third-Party Breaches Deserve Front-Page Attention
Hardened internal defenses can’t stop a weak link upstream. Verizon’s 2025 Data Breach Investigations Report attributes 30% of breaches to third parties, double 2024’s share. According to SecurityScorecard, 98% of organizations maintain at least one relationship with a vendor breached in the past two years.
The MOVEit zero-day shows how fast that danger spreads. One flaw in Progress Software’s file-transfer tool has already affected more than 200 organizations and 17.5 million individuals, according to Axios reporting.
Regulators noticed. The U.S. Securities and Exchange Commission’s July 26, 2023, rule now requires public companies to file an 8-K within four business days after deciding a cyber incident is material. Europe’s NIS2 Directive and the Digital Operational Resilience Act will mandate continuous oversight of critical suppliers starting in 2025.
Third-party risk isn’t a one-time checkbox; it’s a live threat vector that touches every partner in your digital supply chain.

How We Picked the Third-Party Risk Management Software Winners
Real security teams don’t need hype; they need proof. We started by listing the daily pain points we hear from CISOs and procurement leads, the kinds of discovery questions teams ask to truly understand how people work together in a security environment: endless questionnaires, blind spots between audits, and integrations that break at scale. Any vendor that hoped to make our list had to:
- Offer a live, commercially available TPRM module with ≥100 paying customers
- Publish verifiable product-update logs through 2024 and hold SOC 2 or ISO 27001 certification
- Combine automated assessments and continuous risk monitoring (a questionnaire alone isn’t enough)
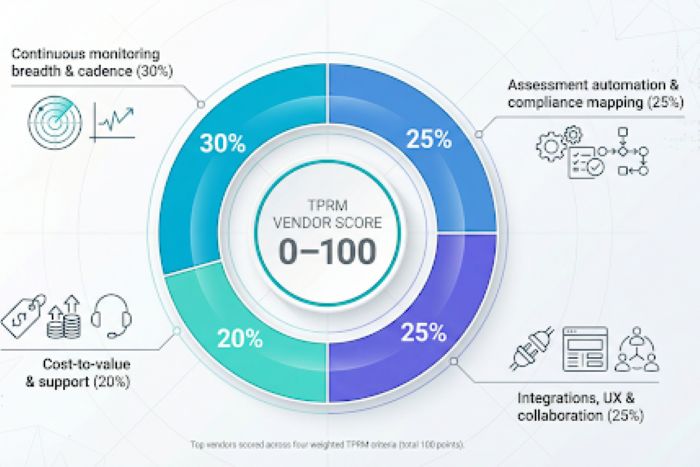
Products that cleared those gates were scored out of 100 across four weighted criteria:
| Metric | Weight |
|---|---|
| Continuous monitoring breadth and cadence | 30 |
| Assessment automation and compliance mapping depth | 25 |
| Integration ecosystem, user experience, and collaboration tools | 25 |
| Cost-to-value ratio and customer support | 20 |
Our team cross-checked analyst reports, vendor documentation, and more than 300 verified user reviews, then validated claims in live demos. The five tools that rose to the top earned their spots on merit, not marketing.
Key Buying-Factor Checklist for Third-Party Risk Management Software
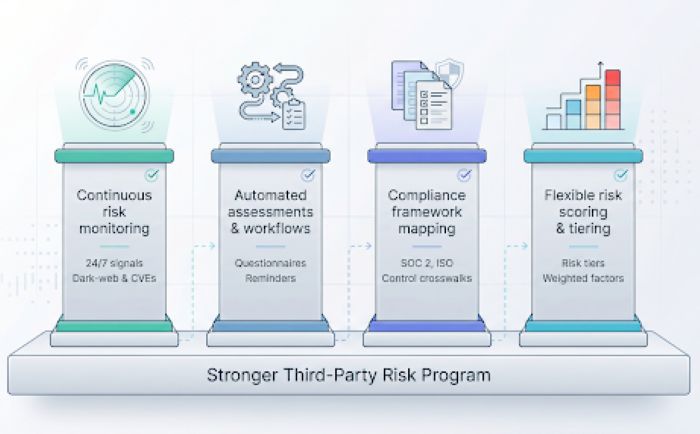
Continuous Risk Monitoring
A one-off questionnaire is stale the moment you hit “send.” Attackers exploit new CVEs within days, yet organizations still need 194 days to identify and 64 more to contain a breach on average, according to IBM’s 2024 Cost of a Data Breach report.
A TPRM platform should shrink that window by continuously:
- Scanning each vendor’s public attack surface for open ports, expired certificates, and leaked credentials
- Tracking breach headlines and fourth-party dependencies in real time
- Pushing high-risk alerts straight into Jira, ServiceNow, or Slack so the right team can act before regulators step in
Prioritize tools that refresh scores every 24 hours, include dark-web and NVD feeds, and log every alert for audit evidence. Live signals turn annual reviews into round-the-clock oversight and give you proof to pause a supplier or demand fixes before the next headline.
Automated Assessments and Workflows
Manual vendor questionnaires can swallow days of back-and-forth email. Embedding AI-assisted automation cuts that churn dramatically; Vanta reports its customers now finish security questionnaires in about one-fifth the time. UpGuard’s Autofill feature has produced similar gains, halving completion time for its own team and saving up to four hours each week.
A strong TPRM workflow should:
- Auto-detect new suppliers from your procurement system
- Launch the right survey based on inherent risk, then chase reminders until every field is done
- Score answers instantly, flag gaps, and route follow-ups to the correct owner with no spreadsheets or copy-paste
Beyond speed, automation builds trust. Each questionnaire version, comment, and remediation note lives in one audit-ready timeline. Quarterly reassessments start on schedule, even if your vendor list doubles, so nothing slips through cracks. Look for tools that include SOC 2, ISO 27001, and GDPR templates yet still let you adjust wording and weighting. When the surveys send themselves, your team can focus on the answers, not the chase.
Compliance Framework Mapping
Auditors speak in controls, not opinions. About 60 to 75% of requirements across major frameworks overlap, according to a 2024 study of multi-framework control libraries. When one vendor answers maps to several clauses, you cut duplicate evidence requests and trim prep time; Clarifire cut audit prep by 50% after adopting cross-mapping in Hyperproof.
A strong TPRM platform should:
- Tag every questionnaire item to SOC 2, ISO 27001, HIPAA, or any custom policy you import
- Check off matching clauses automatically as soon as evidence lands
- Export a one-click report that lists each control, the vendor’s response, and any open tasks
When the EU’s NIS2 or another framework arrives next year, you’ll add a new crosswalk rather than emailing 200 suppliers again. The payoff is immediate: fewer messages, faster audits, and a single source of truth your regulators will accept without pushback.
Flexible Risk Scoring and Tiering
Risk isn’t evenly distributed. SecurityScorecard’s 2024 banking study found that just 6% of vendors were behind incidents that touched 97% of major U.S. banks. A strong TPRM platform lets you focus on that critical slice.
- Start with inherent-risk questions. Data sensitivity, system access, and geography feed an algorithm that places each supplier in critical, high, medium, or low tiers.
- Apply weighted factors. If incident-response maturity matters more than physical security in your industry, move that factor up. The score becomes a documented formula you can show regulators.
- Drive automated actions. Critical vendors trigger deeper questionnaires, quarterly reviews, and proof uploads, while low-risk partners get a lighter check, so your team’s time stays focused where it counts.
Dashboards that stack-rank suppliers by composite score make outliers obvious, helping you allocate remediation hours where they deliver the most value.
Top 5 Picks for Third-Party Risk Management Software
1. Vanta: Best for Automated Compliance and Vendor Trust
Vanta’s third-party risk management module tops our list because it helps security teams spend up to 50% less time on vendor security assessments, and some customers finish questionnaires five times faster. Noibu, for example, trimmed completion from days to hours thanks to AI-generated answers.
Why it stands out
- Compliance DNA. Vanta began in SOC 2 automation, so mapping vendor evidence to ISO 27001, HIPAA, and GDPR feels native. A traffic-light view shows which clauses pass, and you can export an auditor-ready report in seconds.
- Fast, friendly UI. Dashboards load quickly, filter by risk tier, and suggest remediation tasks when a vendor falls short, making life easier for lean teams juggling several frameworks.
Considerations
Vanta’s external attack-surface monitoring is limited. Many customers pair it with a ratings service for continuous scanning.
If your biggest headache is chasing evidence and proving control alignment, Vanta turns a week-long chore into a near-real-time workflow without adding headcount.
2. OneTrust: Best for Enterprise Vendor Risk and Privacy
OneTrust is built for scale: 14,000 customers and 75% of the Fortune 100 rely on its Trust Intelligence Platform. A 2024 Forrester TEI study reports a 227% ROI and a seven-month payback for organizations that adopted OneTrust to unify privacy, GRC, and third-party risk workflows.
Why enterprises choose it
- Adaptive workflows. During onboarding, the platform tailors assessments to the regulations you select—GDPR for a marketing agency, HIPAA for a claims processor, or both. Continuous monitoring then recalculates risk and can automatically launch a full review when news breaks.
- Deep integrations. Because OneTrust sits inside a larger trust-intelligence suite, security findings can flow directly into incident-response playbooks or privacy-impact assessments without copy-paste.
- Portfolio-wide visibility. Role-based dashboards keep legal, security, and procurement aligned while eliminating duplicate data entry.
Considerations
Licensing and professional-services fees climb quickly, and the interface has a learning curve, so smaller teams may find both steep. For global enterprises that need granular control and strong audit trails, however, few rivals match OneTrust’s breadth and financial return.
3. SecurityScorecard: Best for Continuous Cyber-risk Visibility
SecurityScorecard tracks 12 million companies and scans 4.1 billion IP addresses every 24 hours, updating vendor scores daily. Paid customers see about 30% more findings after the 2025 shift to daily scanning, which means open ports, expired certificates, or leaked credentials surface days, sometimes weeks, before a scheduled reassessment.
Why it stands out
- Outside-in grades, A–F. Instant context for the board: an F-rated vendor is 13.8 times more likely to be breached than an A-rated one.
- Fourth-party mapping. Supply-chain graphs reveal hidden dependencies and single points of failure that procurement teams often miss.
- Executive-ready visuals. Trendlines, geographic hot spots, and peer benchmarks turn raw scans into slide-deck gold.
Considerations
Enterprise pricing is steep, and you will still need a questionnaire engine for process controls. Pairing SecurityScorecard with Vanta, OneTrust, or Prevalent gives you both the outside-in radar and inside-out evidence auditors expect.
If real-time threat intelligence tops your list, SecurityScorecard provides the early-warning system that keeps a vendor issue from becoming tomorrow’s headline.
4. UpGuard: Best Mid-Market All-Rounder with AI-assisted Workflows
UpGuard blends outside-in security ratings (zero–950 scale, refreshed daily across millions of organizations) with a questionnaire engine that vendors actually finish. That mix covers most TPRM needs for mid-sized teams without enterprise budgets.
Why it stands out
- AI questionnaire autofill. In October 2024, UpGuard’s upgraded AI completed 77% of a 100-question survey in minutes, and the company’s own sales engineering team cut completion time by half, saving about four hours a week.
- Actionable dashboards. Each vendor’s rating sits next to open remediation tasks, and filters surface high-criticality suppliers with a single click.
- Budget-friendly tiers. Starter plans include ratings, questionnaires, and the AI toolkit, making advanced automation accessible to lean security teams.
Considerations
External scanning depth trails SecurityScorecard’s data lake, and highly customized assessments may require workarounds. For organizations that want continuous ratings, AI-powered surveys, and a friendly UI in one package, UpGuard is a strong mid-market choice.
5. Prevalent: Best for Shared Assessment Libraries and Due-Diligence Speed
Prevalent’s Exchange Network holds risk profiles on more than 310,000 vendors and stores thousands of completed SIG, ISO, and SOC 2 assessments. Members report that 30 to 50% of their suppliers are already in the library, so many questionnaires become one-click approvals instead of week-long chases.
Why it stands out
- Evidence once, share many. Vendors upload certificates and responses once, then grant access to every customer, cutting inbox traffic and vendor fatigue.
- Continuous monitoring included. The platform tracks dark-web credential leaks, breach headlines, and vulnerability chatter across the entire vendor pool.
- Rapid onboarding. Most customers import vendor lists and send first assessments in days, helped by bulk actions and a ServiceNow connector that pushes high-risk findings into existing queues.
Considerations
The proprietary zero-to-100 risk score offers less granularity than letter grades or wider numeric scales, and feature depth cannot match OneTrust or SecurityScorecard. For regulated teams drowning in repetitive questionnaires, however, Prevalent’s shared library turns due diligence from weeks to clicks.
Side-by-Side Snapshot
Need to compare at a glance? The grid below covers the five questions most buyers ask first about third-party risk management software.
| Platform | Continuous monitoring cadence | Questionnaire automation | Framework mapping | Pricing model | Ideal org size |
|---|---|---|---|---|---|
| Vanta | Yes, scope adapts to selected regulations | Yes, with auto-reminders | SOC 2, ISO 27001, GDPR, HIPAA ready | Quote-based tiers | Startup to mid-market |
| OneTrust | Real-time intel feeds, news, and breach alerts | Yes, scope adapts to selected regulations | Largest pre-built library plus custom | Enterprise contracts | Large enterprise |
| SecurityScorecard | Daily scans plus fourth-party discovery | Yes, module maps vendor responses to risk ratings | Overlay available | Free tier plus premium licenses | Mid-market to enterprise |
| UpGuard | Daily scans with prioritized issue list | Yes, AI autofill | Custom fields supported | Transparent SaaS tiers | Mid-market |
| Prevalent | Threat intel plus dark-web checks | Yes, shared evidence exchange | Standard libraries, moderate depth | Subscription plus add-ons | Regulated mid-market |
Which Tool Fits Your Program?
Match the platform to the problem you feel most today.
| Primary pain point | Start with… | Why it helps |
|---|---|---|
| Real-time attack-surface visibility | SecurityScorecard | Daily grades across 12 million companies and fourth-party maps surface threats before scheduled reviews. |
| Auditor-ready evidence and control mapping | Vanta | AI-assisted questionnaires cut completion time by up to five times, and export SOC 2 and ISO reports in seconds. |
| One-stop privacy, GRC, and vendor risk for global groups | OneTrust | Unifies dozens of frameworks; a 2024 Forrester study showed a 227% ROI and a seven-month payback. |
| Mid-market balance of ratings plus surveys | UpGuard | Combines daily scores with AI autofill; starter tier fits most mid-sized budgets. |
| High volume of repeat questionnaires | Prevalent | Evidence-sharing network already covers roughly one-third of suppliers, slashing duplicate outreach. |
Implementation Tips and Next Steps
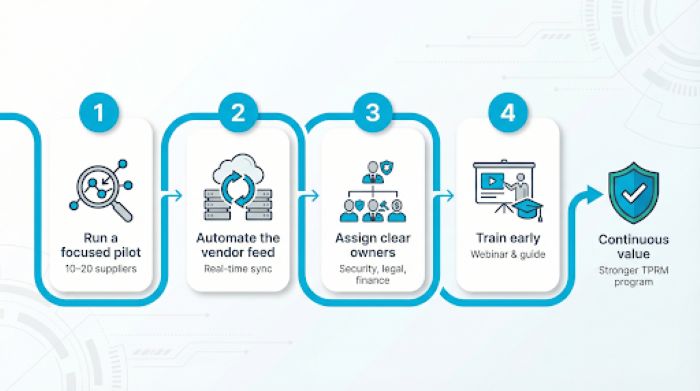
A great platform fails if no one uses it. Follow these four moves, and you will see value quickly:
- Run a focused pilot. Gartner recommends limiting pilots to 10 to 20 suppliers to identify integration gaps while keeping scope manageable.
- Automate the vendor feed. Connect procurement or finance so every new supplier appears in real time; stale lists are the fastest path to unseen risk.
- Assign clear owners. Designating a dedicated vendor risk manager helps ensure one contact per vendor category, security, legal, and finance, preventing duplicate outreach and speeding remediation.
- Train early. A 30-minute webinar and a one-page guide can cut support tickets by 30%, according to customer benchmarks from UpGuard.
Put these basics in place, and the software you choose will deliver the continuous visibility and efficiency promised in the proposal.
Conclusion
Third-party risk management software is no longer optional. By mapping your most urgent pain points to the strengths of each platform, and by planning a disciplined rollout, you can secure your supply chain, satisfy regulators, and free your team from spreadsheet chaos. Shortlist two or three tools from this list, run a focused pilot with your highest-risk vendors, and let the data tell you which platform fits your program best.
FAQ
It is a tool that helps you identify, assess, and monitor the security, privacy, and compliance risks posed by your vendors. It centralizes questionnaires, evidence, scores, and alerts so you are not tracking everything in spreadsheets.
Ownership is usually shared. Security or risk leads the program, procurement owns vendor onboarding, and legal or compliance handles contracts and regulatory requirements.
Start small so you can learn fast. Many teams begin with 10 to 20 high-risk or high-value vendors, refine their workflows, then roll the program out to the rest of the supplier base.
Questionnaires capture how a vendor is supposed to operate. Continuous monitoring shows how they are actually behaving in real time by tracking issues like exposed services, expired certificates, or breach headlines.
Signs include losing track of who has answered which questionnaire, repeating the same evidence requests every audit, and discovering vendor issues after they hit the news. If you have more than a few dozen vendors handling sensitive data, dedicated TPRM software usually pays for itself in saved time and reduced risk.











