Quantum computers are racing toward the power needed to crack Bitcoin’s cryptography—and Wall Street already feels the quake. In January 2026, Jefferies strategist Christopher Wood dropped BTC from his “Greed & Fear” model portfolio, reallocating the slice to gold miners because of quantum risk. If seasoned investors are pivoting, you and I need a countermove—and that begins with understanding quantum-resistant bitcoin tools.
Luckily, developers, hardware teams, and open-source contributors have spent the past two years shipping practical defenses. This guide distills the best post-quantum wallets, blockchains, and hardware so you can lock down your coins long before the first cryptographically relevant machine comes online.
Table of contents
- Why Quantum Computing Threatens Bitcoin
- How We Picked The 2026 Shortlist of Quantum-Resistant Bitcoin Tools
- 1. Project Eleven “Yellowpages”: An Open-Source Quantum Security Registry
- 2. Quantum Resistant Ledger (QRL): A Blockchain Built for the Post-Quantum Timeline
- 3. QANplatform: Hybrid Smart Contracts for Today and Tomorrow
- 4. ZenGo wallet: MPC Convenience with A Quantum-Ready Backbone
- 5. Next-Gen Hardware Wallets: Ledger and Trezor Prepare for Q-Day
- 6. Algorand: A Top-Tier Blockchain Already Running Falcon Under The Hood
- 7. Hedera Hashgraph: Enterprise Governance Meets Rapid-Fire Upgrades
- 8. Other Projects to Watch: Abelian, Starknet, and Bitcoin Cash Vaults
- Bitcoin’s Roadmap to Quantum Resistance
- Conclusion
Why Quantum Computing Threatens Bitcoin
Bitcoin’s security rests on one promise: no one can guess your private key within a useful timeframe. Classical computers keep that promise. Quantum computers cut it short.
A capable quantum processor running Shor’s algorithm can solve the math behind today’s elliptic-curve signatures. Once stable qubit counts reach scale, a thief could lift a public key that appears on-chain and calculate the matching private key in minutes, not millennia.
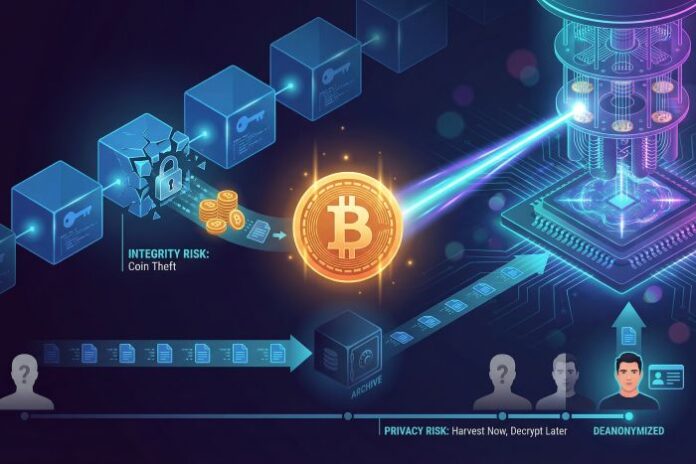
The Federal Reserve sounded the alarm in an October 2025 Federal Reserve report titled “Harvest Now, Decrypt Later.” Researchers warned that attackers are already copying Bitcoin’s full ledger, planning to decrypt it with future machines. A network upgrade tomorrow would not hide data that has already been published.
That risk is two-pronged.
First, integrity: a quantum attacker who forges signatures can move coins held in any address whose public key is visible. Roughly one-quarter of all BTC falls into that bucket, from early Satoshi-period outputs to any wallet you have reused.
Second, privacy: Bitcoin’s pseudonyms work only while the underlying cryptography holds. That is why many early adopters are exploring quantum-resistant bitcoin tools now, rather than waiting for a forced migration later. Project 11’s Yellowpages registry tackles that leak.
During sign-up, your ECDSA-signed message travels inside an AWS Nitro Enclave and a hybrid ML-KEM + AES channel—double encryption that keeps the signature out of any “harvest now, decrypt later” archive.
By treating every signed message as highly sensitive, the tool removes the breadcrumb trail that quantum decryption would otherwise expose.
If the math breaks, every past transaction becomes a breadcrumb that links wallets to real people. The Fed study calls this threat “present and ongoing.” Once the genie escapes, you cannot push it back in.
Hardware is moving faster than most analysts expected. IBM revealed a 1,121-qubit chip in 2023, and Chinese labs demonstrated triple-digit qubit counts with lower error rates in 2025. Industry roadmaps now place a “cryptographically relevant” machine within the next decade.
Upgrading a global, decentralized network takes longer than building a new chip. Taproot needed four years from concept to activation; a post-quantum migration will be harder.
That is why we plan ahead. The tools in the next sections work today, without a protocol hard fork, and help you stay safe long before quantum breakthroughs become practical.
How We Picked The 2026 Shortlist of Quantum-Resistant Bitcoin Tools
Choosing a security tool is an exercise in trust. We ignored glossy marketing and built one yardstick to measure every contender.
First, we required open code or a published, third-party audit. If the math stays hidden, the claims stay unproven. Next, we checked cryptographic strength: Dilithium, Falcon, SPHINCS+, and other hash-based schemes outscore any closed, “proprietary magic.”
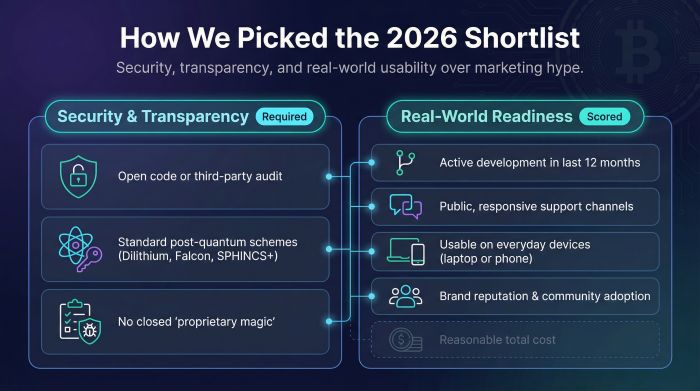
Development pace mattered. Dormant GitHub repositories and silent support channels raise red flags, so we favored projects that shipped updates within the past 12 months and answered users in public.
We also scored real-world usability. Any wallet that needs four terminal windows and a PhD stays on the shelf; we want tools you and I can run on a laptop or phone today. Brand reputation, community adoption, and total cost completed the scorecard.
Those filters cut our longlist from 20 projects to eight clear winners. Each one adds a tangible layer of quantum defense without pulling you out of Bitcoin’s ecosystem.
1. Project Eleven “Yellowpages”: An Open-Source Quantum Security Registry
Project Eleven Yellowpages Quantum-Resistant Bitcoin Ownership Registry UI.
Yellowpages works like a notarized will for your Bitcoin: you sign a short message with your current key, pair it with a fresh Dilithium public key, and publish the proof in a public, time-stamped registry. The project’s launch write-up calls this “five-minute” quantum security that locks in ownership today without moving coins or waiting for a contentious hard fork.
You sign a short message with your current key, pair it with a fresh post-quantum public key, and publish the proof in a public registry. No coins move, and the protocol stays untouched. Yet you now hold a time-stamped record that links your BTC to credentials a quantum thief cannot forge.
The concept is simple: connect today’s vulnerable address to tomorrow’s safe one while you still control both secrets. Because Project 11 yellowpages keeps the code free, audited, and open source, anyone can review the math or host a mirror of the registry. According to Project Eleven, Yellowpages targets holders who expect to ride Bitcoin past “Q-Day” without waiting for network politics to catch up.
2. Quantum Resistant Ledger (QRL): A Blockchain Built for the Post-Quantum Timeline
Quantum Resistant Ledger (QRL) Official Website and Quantum-Safe Branding.
Most projects bolt on security after a scare. QRL did the opposite. It launched in 2018 with hash-based XMSS signatures baked into every address, so the ledger can survive even an aggressive quantum schedule.
Using QRL feels familiar: download the wallet, create an account, and send tokens as you would on any chain. The difference sits under the hood. Each spend uses a one-time, post-quantum signature that a quantum computer cannot forge. Attackers gain no shortcut, regardless of qubit count.
Developers raised the bar again in 2025 by adding an EVM-compatible layer to the quantum-safe core. Smart contracts and NFTs now live on a foundation already armored for what comes next.
For Bitcoin holders, QRL is not a direct shield but a hedge. Moving a slice of long-term savings into a ledger designed to resist Shor’s algorithm buys peace of mind, and it provides a live demonstration of how a future Bitcoin upgrade could work.
The trade-off is liquidity. QRL’s user base is small compared with Ethereum, so you surrender market depth for added resilience. If your priority is sleeping well in 2035, that swap feels worthwhile.
3. QANplatform: Hybrid Smart Contracts for Today and Tomorrow
QANplatform uses a two-layer approach. Every account stores two key pairs: one familiar ECDSA key for compatibility, and one lattice-based Dilithium key for the post-quantum horizon. When you submit a transaction, the network checks both signatures at once.
This design lets developers ship DeFi apps today while future-proofing the assets beneath them. If quantum machines break elliptic curves, QAN nodes can ignore the legacy half of each signature without touching any contract code.
The chain is young and still heading toward mainnet, yet the architecture tackles a real pain point: migrating complex smart-contract logic without pausing the economy that runs on it. By packaging both generations of cryptography into every call, QAN makes the eventual switch a simple toggle rather than a fork that splits liquidity.
Early adopters accept two trade-offs: lower transaction throughput while Dilithium libraries mature, and thinner liquidity than on Ethereum. In return, they gain a live sandbox to test quantum-safe contracts years before the deadline. For builders who expect to be here after 2030, that exchange is worth it.
4. ZenGo wallet: MPC Convenience with A Quantum-Ready Backbone
Seed phrases stop casual hackers, yet they leave one brittle point of failure. Lose the words, or let malware grab a screenshot, and your coins walk away.
ZenGo replaces that single secret with multi-party computation. Your phone stores one key share, ZenGo’s server the other. Neither side ever sees the full private key, so no thief can seize it wholesale, even with quantum power.

ZenGo MPC Crypto Wallet Mobile App Interface Screenshot.
MPC also gives ZenGo a clean upgrade path. Because signing is already distributed, the team can swap the underlying math from ECDSA to Dilithium without changing how you tap “Send.” Users keep the same interface; attackers meet a fresh wall of cryptography.
Everyday usability is the headline. No seed phrase to stash, FaceID unlocks the wallet, and cloud backup restores it if you drop your phone in a lake. For many newcomers those comforts beat writing 12 random words on paper.
The downside is partial reliance on ZenGo’s servers. If they disappear, recovery takes longer. Still, for holders who prize simplicity and future-proofing in one app, ZenGo delivers both.
5. Next-Gen Hardware Wallets: Ledger and Trezor Prepare for Q-Day

Ledger Nano X and Trezor Model T Quantum-Ready Hardware Wallets.
Hardware wallets solve the oldest crypto headache: keeping keys offline. The top brands now focus on the newest threat, quantum theft.
Ledger’s secure element accepts new firmware without opening the case. Engineers are coding a post-quantum signature that sits beside today’s curve. When the update arrives, you plug in, install it, and move coins to fresh addresses. Same device, stronger protection.
Trezor leans on its open-source roots. Community developers test Falcon and Dilithium builds in public, so anyone can review the math. After a version proves stable, one firmware flash upgrades every Model T.
For now, your checklist stays simple: use a hardware wallet and quantum-resistant bitcoin tools, keep firmware current, and plan to rotate funds when the manufacturer ships its quantum-ready release. The habit takes minutes and can protect a lifetime of savings.
6. Algorand: A Top-Tier Blockchain Already Running Falcon Under The Hood
Algorand was created by Turing Award winner Silvio Micali, so forward-looking cryptography sits at its core. In 2024 the network quietly activated Falcon signatures inside its state-proof system. This change means the bridges and light-client checks that link Algorand to other chains already rely on post-quantum math.
Everyday transfers still use classical Ed25519 keys for speed, yet the upgrade path is open. Governance can vote to make Falcon the default without touching the consensus engine. For holders, that promises future security with no extra steps. You keep pressing “Send”; the protocol handles the rest.
Proof-of-stake adds another shield. With no mining, quantum rigs gain nothing by brute-forcing hashes; the only viable target is the signature layer, and that layer is already halfway to quantum-safe.
If you want exposure to a liquid chain that treats quantum risk as an engineering deadline, Algorand belongs on your watchlist.
7. Hedera Hashgraph: Enterprise Governance Meets Rapid-Fire Upgrades
Hedera runs on hashgraph, a gossip protocol that reaches finality without proof-of-work puzzles. Quantum computers gain nothing by crunching its consensus, so the weak spot is the signature on each user account.
That happens to be the easiest part for Hedera’s governing council to replace. Because 40-plus blue-chip firms steer the network, a super-majority can vote a new post-quantum algorithm into production as soon as standards settle. No long dispute, no fork drama, just a scheduled maintenance window.
Enterprises building supply-chain or identity apps on Hedera value that certainty. They need to know their ledgers will keep running for decades, no matter what breakthroughs arrive in physics.
For individual holders, Hedera offers a different flavor of quantum defense: trust in agile governance rather than trust in pure code. If you believe human coordination can outpace silicon advances, staking a small HBAR position is worth considering.
8. Other Projects to Watch: Abelian, Starknet, and Bitcoin Cash Vaults
Quantum preparedness with quantum-resistant bitcoin tools is no longer niche. It is spreading across privacy coins, Ethereum-style roll-ups, and even Bitcoin’s cousins.
Abelian pairs lattice cryptography with privacy layers, aiming to keep sender and amount opaque even when quantum decryption arrives. The network is small today, yet it demonstrates how post-quantum math can sit beside zero-knowledge tools without hurting performance.
StarkNet already proves that point. Its STARK proofs rely on hash functions, which shrug off Shor’s algorithm by design. Users who bridge assets onto the roll-up enjoy quantum-secure validity now, while the underlying Ethereum layer works toward its own upgrade.
Developers on Bitcoin Cash took a different tack. Their Quantumroot vault proposal wraps coins in Lamport one-time signatures. Spend once and the address self-destructs, denying attackers a public key that lingers on-chain. The feature rides a scheduled soft fork, offering a live model of how Bitcoin itself could adopt quantum-safe outputs.
None of these experiments is as mature as the tools above, but each adds new ideas to the playbook. Keep them on your radar; one of them might spark the breakthrough that lands in Bitcoin Core.
Bitcoin’s Roadmap to Quantum Resistance
Bitcoin is not blind to the ticking clock. Core developers, academics, and wallet authors have debated fixes for years on the bitcoin-dev list. The emerging goal is simple: replace today’s elliptic-curve signatures with a hash-based or lattice alternative before quantum hardware can weaponize Shor’s algorithm.
Two draft BIPs map the route. The first adds an optional output type that accepts a post-quantum signature. Think of it as SegWit for the quantum age. Early adopters could move coins the day the feature ships, while the rest of the network keeps running on legacy keys. The second proposal schedules a sunset for old addresses: after a three-year grace period, miners would stop relaying transactions that rely on broken math.
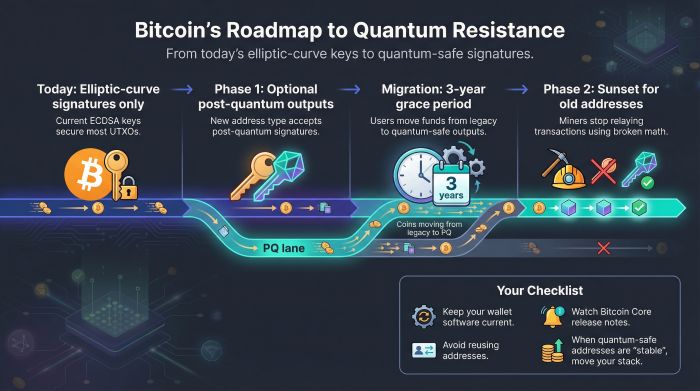
Those levers only work if people pull them. The checklist is short: keep your wallet software current, avoid reusing addresses, and watch the release notes. When Bitcoin Core marks a quantum-safe address format as “stable,” move your stack. The migration should feel like the shift to SegWit or Taproot—familiar, uneventful, and critical.
Conclusion
Until then, the external tools we covered act as life jackets. They buy time so you are not racing the clock when the final upgrade notice arrives. Exploring and adopting quantum-resistant bitcoin tools now gives you agency, flexibility, and a strategic advantage—long before quantum computing becomes an immediate threat.