Nearly half of enterprises admit they’re unprepared for quantum threats—48 percent, according to Keyfactor’s 2025 survey of cybersecurity leaders. Once practical quantum computers come online, RSA and ECC could fall in hours, not years, and attackers are already stockpiling traffic to decrypt later. The fastest remedy is a quantum risk assessment.
It inventories every algorithm, certificate, and protocol you rely on, scores each against Shor’s algorithm, and delivers a phased roadmap to swap in NIST-approved, quantum-safe options—think of it as a cryptographic MRI that spots silent weaknesses before they metastasize.
In this guide, you’ll find:
- A quick refresher on the quantum threat landscape and current government mandates
- The criteria we used to rank today’s top assessment providers
- Ten concise, service-by-service reviews—from boutique blockchain experts to Big-4 heavyweights
- A comparison snapshot and buyer’s checklist that map partners to budgets and compliance pressure
- Rapid-fire FAQs that clear up common misconceptions before they stall your project
Early adopters are already moving—Solana’s post-quantum testnet proves you can upgrade without killing performance. Ready? Here’s what to expect.
Key Takeaways
- 48% of enterprises feel unprepared for quantum threats; quantum computers could break encryption quickly.
- Conducting a quantum risk assessment identifies vulnerable algorithms and provides a roadmap to quantum-safe options.
- Organizations must adhere to NIST standards and government mandates for migrating to quantum-safe algorithms.
- Top providers offer various strengths, from deep cryptographic expertise to large-scale implementation, aiding in transitioning to quantum security.
- A proactive approach to quantum risk assessment is crucial; waiting until after quantum computers are operational can leave sensitive data exposed.
Table of contents
- Why Quantum Risk Assessment Is Critical
- How We Chose the Best Services
- 1. Project Eleven: Blockchain’s Post-Quantum Bodyguard
- 2. Deloitte: Enterprise-Grade Quantum Readiness
- 3. Accenture Security: From Strategy To Hands-On Integration
- 4. Evolutionq: Cryptography Pioneers on Speed-Dial
- 5. Applied Quantum: Governance First, Tech Second
- 6. Tata Consultancy Services: Mass-Scale Migration for the Enterprise Stack
- 7. Kudelski Security: Crypto Roots, Quantum Future
- 8. Sandboxaq: Automation at Quantum Speed
- 9. Protiviti: Risk Lens, Board Language
- 10. Keyfactor with Infosec Global: Crypto Agility as a Service
- How The Top Providers of Quantum Risk Assessment Stack Up
- Buyer’s Guide: Choosing The Right Partner for Quantum Risk Assessment
- Frequently Asked Questions
- Conclusion
Why Quantum Risk Assessment Is Critical
Quantum computing is no longer a lab curiosity. Venture funding, qubit counts, and error-correction breakthroughs accelerate each quarter. The window keeps shrinking before a “crypto-relevant” machine can shred RSA and ECC in hours.
NIST took the hint. On August 13, 2024, the agency finalized three Federal Information Processing Standards (FIPS 203, 204, and 205) that adopt Kyber for key exchange and Dilithium and Sphincs+ for signatures.
Governments followed. The United States now requires every federal agency to inventory vulnerable encryption and publish a migration plan, while the NSA’s CNSA 2.0 profile pushes national-security systems to adopt quantum-safe algorithms by 2035. Similar directives echo across Europe through ENISA and ETSI. Regulators are no longer asking if you will migrate; they want to know how fast.
Attackers are not waiting. Intelligence services capture today’s VPN traffic, confident they can decrypt it later. Financial records, medical histories, and blockchain keys all need to stay secret for decades, which means they are already at risk in 2026.

That is why a formal quantum risk assessment matters. It lists every certificate, protocol, and hard-coded algorithm you rely on, then maps each one against NIST standards and regulatory deadlines. The outcome is a phased, budget-aware roadmap that keeps your crown-jewel data confidential long after quantum computers reach scale.
Skip the assessment and you gamble with blind spots. Run it and you swap uncertainty for a clear schedule, a budget line, and—most important—encryption that will still work when a quantum computer finally boots up.
Real-world pilots underscore that urgency.
Project 11’s Quantum Readiness Levels framework flags Bitcoin and Ethereum at “Level 5 – Minimally Secure,” a category reserved for systems that still rely exclusively on classical RSA or ECC keys.
In December 2025 the firm also partnered with the Solana Foundation to run a Dilithium-based testnet and reported that fully quantum-resistant transactions remained “practical and scalable” on production-grade hardware. Together those data points show why a discovery-driven assessment should start now, not after Q-Day.
How We Chose the Best Services
Any top-ten list is only as good as the yardstick behind it, so we built ours first.
We began with a long list of twenty global providers—boutique cryptography shops, Big-4 consultancies, and product-led vendors. Each name was graded against six weighted factors: depth of cryptography expertise, quality of automated tools, end-to-end service scope, alignment with NIST and other standards, real-world track record, and pricing transparency.
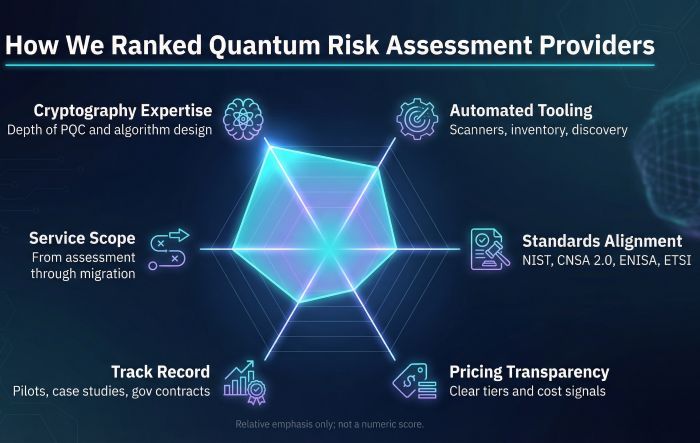
Expertise carried the most weight. Post-quantum cryptography leaves little room for error, so teams with published cryptographers scored higher than firms that rely solely on generalists. Tooling came next. Automated scanners that locate every stray RSA-2048 key save time and raise accuracy, especially across sprawling networks.
Service breadth also mattered. A firm that only delivers a slide deck, not migration help, scored lower than one that owns the path from inventory to rollout. We further rewarded providers who map recommendations to hard regulations, because boards want compliance, not theory.
Track record keeps hype in check. We looked for named case studies, pilot projects, or government contracts that prove the service works in production. Finally, we noted how clear each company is about cost. Nobody expects fixed pricing for a global bank, but starter packages or published tiers show helpful confidence.
The outcome is a transparent scoring matrix, not a popularity contest. In the next section you’ll meet the ten providers that cleared the bar and learn why each earned its slot on the list.
1. Project Eleven: Blockchain’s Post-Quantum Bodyguard
Project Eleven post-quantum Solana testnet official webpage screenshot
Project Eleven focuses on a niche that most providers avoid: securing public blockchains and digital-asset platforms before quantum attacks can steal private keys. The New York team proved its skill by collaborating with the Solana Foundation in December 2025 to run a full post-quantum testnet that swapped Ed25519 signatures for Dilithium without slowing transaction throughput. In a December 16 2025 bulletin titled Solana Post-Quantum Security, Project Eleven dissects that Dilithium-signed Solana testnet and shares benchmark data showing quantum-resistant transactions remained practical and scalable on production-grade hardware.
Unlike firms that deliver only a slide deck, Project Eleven ships working code. Consultants start with a cryptographic MRI of your chain or custody system, pinpoint where keys, wallets, and signing flows fail under Shor’s algorithm, and then prototype quantum-safe upgrades in a sandbox so engineers see real performance numbers.
Strengths include deep cryptography talent paired with hands-on blockchain engineering. Because the firm is boutique, large enterprises may need a second partner for wide IT estates. Still, if digital assets appear anywhere on the balance sheet, Project Eleven offers proof, not promises—precisely what boards want when billions in token value are at stake.
2. Deloitte: Enterprise-Grade Quantum Readiness
Deloitte quantum cyber readiness services official page screenshot
Deloitte handles quantum risk the same way it approaches financial audits or SAP rollouts: a global playbook, large teams of specialists, and zero tolerance for surprises.
Engagements start with a cryptography inventory that scans everything from mainframes to microservices, then funnels findings into a board-ready risk heat map. From there, Deloitte architects design a phased migration, slotting Kyber or Dilithium into existing PKI workflows and preparing budget forecasts so CFOs nod instead of wince.
What sets the firm apart is its depth of bench. Compliance professionals translate NIST guidance into policy, software engineers retrofit legacy code, and PMOs keep a 1,000-line Gantt chart on schedule. That breadth makes Deloitte the safe pick when regulators or shareholders demand progress you can document.
The trade-off is cost. You pay Big-4 rates and accept a methodical pace. Yet for multinational banks, insurers, and critical-infrastructure operators, that rigor is a benefit, not a drawback. If your board wants quantum risk off the audit-committee agenda next quarter, and documented down to the last certificate, Deloitte checks every box.
3. Accenture Security: From Strategy To Hands-On Integration
Accenture treats quantum risk as it does any digital transformation project: assess, architect, then embed the fix in live production.
Work begins with a “Quantum Impact Workshop,” where executives map long-life data and compliance deadlines. Accenture’s cyber team follows with tool-assisted discovery, often built on tech from QuSecure, a startup in which Accenture invested to speed crypto agility. Your first report therefore includes concrete remediation options, not just red flags.
Execution is where Accenture shines. The same engineers who guide zero-trust or cloud-native migrations can retrofit applications to use Kyber and Dilithium, update HSM firmware, and roll out hybrid TLS across global data centers. One project for the U.S. Space Force even tested post-quantum encryption over satellite links, showing the firm can handle edge cases as well as core IT.
Pricing sits at the premium end, but you get start-to-finish accountability, from board slide to code commit, which suits on-prem, multi-cloud, and OT environments that need crypto agility now.
4. Evolutionq: Cryptography Pioneers on Speed-Dial
If you want the scientists who helped invent post-quantum cryptography reviewing your systems, evolutionQ is the call to make. Co-founded by Dr. Michele Mosca of the University of Waterloo’s Institute for Quantum Computing, the firm blends deep academic pedigree with practical consulting.
An engagement starts with a plain-English briefing for executives, no math PhDs required, followed by a forensic sweep of every algorithm your business relies on. The team then delivers a quantum-safe action plan ranked by data shelf life and regulatory pressure, complete with interim controls such as hash-based signatures for code signing while you migrate.
Clients praise evolutionQ for intellectual honesty. If a standard is still maturing, they state the risk instead of hiding it in footnotes. Team members serve on NIST and ETSI working groups, so recommendations reflect the latest drafts, not last year’s blog posts.
The firm is boutique by choice, so you hire them for strategy and validation, then lean on internal staff or an integrator to roll out fixes at scale. When the stakes include national-security contracts or multi-billion-dollar data troves, having the original researchers review your plan is worth every invoice line.
5. Applied Quantum: Governance First, Tech Second
Applied Quantum approaches post-quantum security the way risk officers prefer: start with governance, add the technology after the rules are clear. Day-one workshops align CISOs, lawyers, and developers around one question, “Which data still matters ten years from now?”
The team then builds a Cryptographic Bill of Materials your auditors can read, ranks each system by business impact, and drafts a phased transition plan with staffing and budget lines. Training is woven in so developers understand why Kyber matters before they paste a new library into code.
Because Applied Quantum stays tool-agnostic, you receive a plain-spoken shopping list of scanners and HSM upgrades instead of a hard sell. The firm is smaller than the Big-4, yet the principal consultant you meet in week one is still on the call when the board signs off months later.
6. Tata Consultancy Services: Mass-Scale Migration for the Enterprise Stack
TCS applies the same disciplined playbook it uses for core banking and telco billing to post-quantum security: structured frameworks, proven accelerators, and large teams of engineers who can refactor legacy code at scale.
Engagements start with a readiness workshop tailored to regulators such as RBI or GDPR, then shift to tool-assisted discovery across thousands of applications. TCS accelerators produce a ranked list of crypto dependencies, while industry specialists convert that list into sprint backlogs any scrum team can execute.
Volume is where TCS excels. Need 500 Java services shifted to a hybrid Kyber-TLS handshake by year-end? Teams across three continents handle the workload and still meet change-control windows. Costs stay competitive thanks to offshore talent, and governance remains tight through ISO-aligned processes.
If you manage a sprawling IT estate in finance, telecom, or government and want quantum remediation folded into broader digital transformation timelines, TCS provides the capacity and methodology to get the job done.
7. Kudelski Security: Crypto Roots, Quantum Future
Kudelski built its reputation protecting satellite TV streams from pirates, so dissecting encryption sits at the center of the company’s culture. Its Quantum Computing Security Assessment applies that hardware-grade scrutiny to corporate networks.
The process starts with context: what data needs to stay secret for decades? Consultants then deploy proprietary scanners from Kudelski’s cryptography lab to map every cipher, key length, and protocol. Findings arrive in a dashboard that color codes urgent fixes and recommends quick wins, such as swapping RSA-2048 VPN tunnels for hybrid Kyber handshakes.
Clients value the follow-through. The same engineers return to update HSM firmware, rewrite certificate policies, and retest until no legacy algorithm slips back into production. One global bank used Kudelski’s action plan to re-encrypt archival backups without taking core systems offline.
Coverage is strongest in finance, media, and critical infrastructure. Smaller companies may see the service as more than they need, but if you prefer a technician’s eye to a strategist’s overview, Kudelski is a safe pair of hands.
8. Sandboxaq: Automation at Quantum Speed
SandboxAQ AQtive Guard cryptographic posture management platform homepage screenshot
SandboxAQ, an Alphabet spin-off, swaps clipboards for code. Its AQtive Guard platform passively inspects live network traffic, inventories every cipher in use, and flags weak links in near real time. Picture Shodan applied to your own encryption estate.
Deploy the sensor, wait a week, and you receive a heat-mapped dashboard plus automated playbooks that insert hybrid Kyber handshakes without dropping sessions. The same software enforces policy going forward, blocking new services that attempt to use outdated RSA. Built-in quantum risk assessment capabilities continuously evaluate cryptographic exposure and prioritize remediation based on real-world impact.
Former Google cryptographers fine-tune rollouts and sanity-check edge cases such as post-quantum Wi-Fi roaming or high-frequency-trading latency caps. The technology already protects U.S. Department of Defense networks, which speaks to its scalability and trust.
Pricing arrives as an annual subscription with optional consulting, so budget owners know the number before paperwork starts. If you need speed, data-driven accuracy, and controls that persist long after the consultants leave, SandboxAQ offers a rare set-and-forget option.
9. Protiviti: Risk Lens, Board Language
Protiviti places quantum risk on the same enterprise-risk matrix your audit committee reviews each quarter. Workshops translate cryptographic jargon into likelihood-and-impact scores, then plot those scores beside ransomware, supply-chain, and regulatory risks. Boards see quantum as a business issue, not science fiction.
Consultants gather crypto inventory through questionnaires and targeted scans, but the real value shows up in governance detail. Expect a refreshed risk register, updated control objectives, and a step-by-step roadmap mapped to ISO and NIST frameworks. Because Protiviti’s roots lie in internal audit, every recommendation includes evidence paths—ideal for future compliance reviews.
The firm avoids selling tooling or managed services; instead, it partners with the scanner or HSM vendor that best fits your stack. That neutrality and the audit-ready documentation make Protiviti a smart pick for mid-market companies that need to reassure regulators and investors without hiring a full cryptography team.
10. Keyfactor with Infosec Global: Crypto Agility as a Service
Keyfactor built its name managing millions of digital certificates for Fortune 500s. After acquiring InfoSec Global, it paired that PKI strength with AgileSec, a platform that scans every algorithm, library, and hard-coded key across code repositories, containers, and IoT fleets. The platform also incorporates quantum risk assessment to quantify exposure and prioritize remediation across complex environments.
The flow is automated. Point AgileSec at your environment and, within hours, you see a dashboard that flags TLS endpoints still using RSA-2048, firmware images embedding ECC, and places where quantum-safe options are already live. Keyfactor’s lifecycle tools then bulk-replace certificates with Kyber hybrids and enforce policy so developers cannot reintroduce outdated ciphers.
Consulting is offered à la carte. Cryptographers from the InfoSec Global team review edge cases, design migration playbooks, and confirm that performance stays within SLAs. Pricing combines a clear subscription with professional-services blocks, making budget approval easier than open-ended consulting bids.
If your biggest challenge is scale—tens of thousands of certificates, millions of devices, or nonstop CI/CD pipelines—Keyfactor provides a data-driven path to quantum-safe crypto that keeps working long after the first migration wave ends.
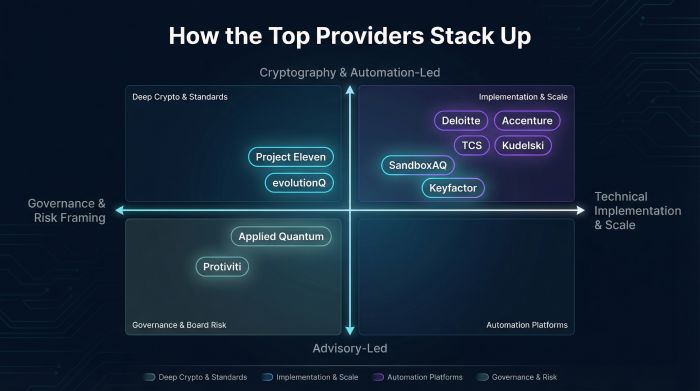
How The Top Providers of Quantum Risk Assessment Stack Up
Each of the ten services excels in a different lane, so the choice depends on what you need most: deep cryptography research, large-scale implementation, real-time automation, or board-friendly risk framing.
Project Eleven and evolutionQ win on raw cryptographic brainpower; their founders help steer global standards, making them ideal when you need algorithm advice no one else can give. Deloitte and Accenture dominate breadth; they bring governance consultants, coders, and change-management leads under one roof, which suits multinationals facing heavy regulatory pressure.
If speed and telemetry top your wish list, SandboxAQ and Keyfactor stand out. Both deliver always-on platforms that surface weak ciphers and enforce policy long after the initial quantum risk assessment. TCS and Kudelski specialise in scale and technical depth: TCS for refactoring thousands of apps, Kudelski for hardware-level crypto surgery. Finally, Applied Quantum and Protiviti focus on governance first, translating quantum jargon into risk registers and budget lines that boards can approve.
Below is a quick snapshot to help match needs to strengths:
| Provider | Core strength | Ideal for |
| Project Eleven | Blockchain PQC prototypes | Crypto and fintech firms |
| Deloitte | End-to-end, global compliance | Fortune 500, government |
| Accenture | Integration and managed services | Multi-cloud enterprises |
| evolutionQ | Academic-grade expertise | Critical infrastructure |
| Applied Quantum | Governance-centric roadmaps | Mid-market, regulated |
| TCS | Large-scale code migration | Banks, telecoms |
| Kudelski | Hardware-level crypto fixes | Finance, media |
| SandboxAQ | Automated network scanning | Large, dynamic fleets |
| Protiviti | Board-ready risk framing | Audit-heavy industries |
| Keyfactor | Certificate lifecycle and IoT | Device manufacturers |
Use this grid as a shortcut, then return to the mini-reviews for details that fit your own risk profile, budget, and talent pool.
Buyer’s Guide: Choosing The Right Partner for Quantum Risk Assessment
Start by sizing up your own house. Do you already run a PKI team and DevSecOps pipeline, or is encryption scattered across shadow IT? An honest self-audit shows whether you need raw cryptography talent, mass-scale engineering, or a product that watches keys around the clock.
Next, match your risk horizon to provider style. If you protect data that must stay private for decades, such as patient files, financial records, or blockchain keys, look to evolutionQ or Project Eleven for deep algorithm guidance. Facing a regulator’s fixed deadline? Deloitte, Accenture, and Protiviti bring board-ready frameworks that stand up to audit scrutiny. Need to update thousands of microservices within months? Automation-first vendors like SandboxAQ and Keyfactor shorten the schedule.
Finally, pressure-test shortlists with direct questions. The answers reveal culture as much as capability:
- Which automated tools will we see results from in week one?
- How do you map findings to NIST FIPS 203, 204, and 205 and to our industry regulations?
- Can you share an anonymized deliverable from a similar client?
- Who owns remediation—your team, ours, or a hybrid model?
- What does year-two support look like once the initial Quantum risk assessment ends?
A strong partner answers with specifics, not abstractions. They quote timelines, name the engineers on call, and outline clear success metrics. When every response feels concrete, you have found the right ally for the quantum race.
Frequently Asked Questions
When do we need to act on quantum threats?
Today. Data encrypted now can be stored and cracked later, and regulators already expect migration plans. Waiting for a fault-tolerant quantum computer leaves no time to swap algorithms or retrain teams.
Is a quantum risk assessment different from a normal cyber audit?
Yes. Traditional audits look for current exploits such as open ports or unpatched servers. A quantum risk assessment inventories every algorithm, certificate, and key to judge how long each remains secure once Shor’s algorithm becomes practical. It delivers forward-looking resilience rather than present-day hygiene.
Can we handle the work internally?
Only if you employ seasoned cryptographers. Most organizations lack staff who track NIST drafts and understand performance trade-offs of Kyber versus Dilithium. External assessors bring tested playbooks, automated scanners, and migration schedules that prevent costly trial and error.
What does a typical project cost?
Prices vary by scope. Boutique strategy shops may charge a fixed fee in the mid-five figures. Big-4 consultancies and product-plus-service vendors often quote six to low-seven figures for multi-year programs that include tooling and remediation. Re-issuing certificates after a breach can cost far more than proactive planning.
Will post-quantum algorithms slow my applications?
Early benchmarks show modest overhead, often single-digit milliseconds per handshake for Kyber or Dilithium. Most providers recommend hybrid modes first, combining classic and PQC algorithms so you gain future-proofing without breaking latency-sensitive systems.
What about Quantum Key Distribution?
QKD works best for point-to-point, high-value links such as inter-data-center fiber. For broad IT estates, software-based PQC is usually more practical. All ten providers in our list focus on PQC first and will advise if, when, and where QKD makes economic sense.
Conclusion
Keep these answers handy when you brief leadership; they condense hours of technical debate into executive-level clarity.











