Today, about 32.7 percent of all BTC—roughly 6.36 million coins—sit in addresses whose public keys are already public, making them easy prey for a future Shor’s-style attack. When applied-security labs such as Project 11 run chain-wide scans, build migration tools, and share clear guidance, you see what it really takes to harden a decentralized network and defend Bitcoin before the next class of threats arrives.
Key Takeaways
- Approximately 32.7% of all BTC is vulnerable to quantum attacks due to exposed public keys.
- Measuring risk involves creating dashboards to analyze blockchain vulnerabilities and estimate loss projections.
- To ensure successful migration to quantum-safe solutions, projects must combine user experience design with cryptographic security.
- Collaboration between quantum physicists and crypto developers is essential for overcoming technical barriers in implementing solutions.
- The need for quantum safety goes beyond Bitcoin; it impacts web payments, identity systems, and various Layer-2 networks.
Table of contents
Measuring Risk Before Fixing It
Before you change a single line of code, you need a scoreboard. Recent chain-wide scans by Chaincode Labs, the Human Rights Foundation, and open dashboards such as Project 11’s Bitcoin Risq List show that roughly 6.3–6.5 million BTC, about one-third of the supply, already sits in addresses whose public keys are exposed, according to Ainvest. More than 69 percent of that vulnerable pot (≈4.5 million BTC) stems from ordinary address reuse, the same analysis finds.

A scoreboard-style dashboard turns abstract quantum threats into concrete blockchain risk metrics.
To surface those hot spots, quantum-readiness teams typically:
- Data pipelines that replay every block and flag addresses once a spend reveals the public key.
- Interactive dashboards so you, along with custodians, exchanges, or auditors, can see how much value is at risk in real time.
- Scenario models that map timelines (for example, 5-, 10-, and 15-year CRQC forecasts) to loss projections.
For Bitcoin, Ethereum, and other UTXO- or account-based chains, that workflow means classifying each address type, spotting key reuse the moment it happens, and stress-testing how different quantum attack strategies could drain funds if owners stay put.
In short, measurement turns an abstract “quantum threat” into a timestamped ledger of who needs to move first to defend Bitcoin, and how urgently.
Designing Migration Paths, Not Just Algorithms
Writing a quantum-safe signature scheme may take months in a lab, but persuading millions of holders to use it can take years. Bitcoin’s history proves the point: SegWit needed nearly eight years—from its 2017 activation to mid-2025—to reach 77 percent of blocks, according to Coindesk, while Taproot, live since late 2021, still appears in fewer than 10 percent of spent outputs, according to Glassnode. Those adoption curves exist without the pressure of a quantum deadline.
That is why migration engineering focuses less on math and more on experience:
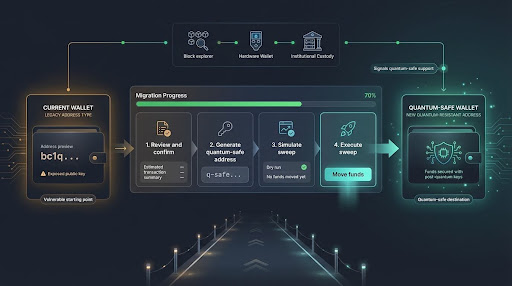
Thoughtful migration design guides holders from legacy Bitcoin addresses to quantum-safe wallets without breaking existing tools.
- Safe, step-by-step workflows to defend Bitcoin so you can sweep funds without worrying about typos or fee shocks.
- Network-wide signaling (think BIP-style registries or on-chain flags) that lets wallets advertise their new, quantum-resistant address before they spend.
- Backward-compatible bridges so explorers, hardware wallets, and custody platforms keep working as users move over.
In practice, protocol teams prototype the user experience first and harden the cryptography afterward. A flawless algorithm is pointless if the “move” button feels risky or confusing. Building that runway, complete with guard rails, status lights, and roll-back options, turns a theoretical fix into a real-world migration.
Experimenting in Public
“We only trust crypto that survives a beating.” That mindset drives you and every serious lab to keep work in the open.
Since NIST opened its post-quantum contest in 2016, researchers have submitted 82 algorithms; by 2023 the agency had trimmed its digital-signature track from 40 entries to 14 second-round candidates, according to NIST. When the isogeny-based scheme SIKE collapsed in just one hour on a single-core PC, earning the attackers a $50 k Microsoft bounty, Ars Technica reported why daylight matters.
Labs that take quantum threats seriously now:
- Sponsor break-me challenges (cash prizes, conference workshops) that stress-test fresh code before it reaches wallets.
- Simulate chain-wide attacks to estimate how fast an exposed-key sweep could drain Bitcoin or Ethereum.
- Publish tooling and metrics on GitHub so anyone—yes, even you—can rerun the scans or fork improvements to defend Bitcoin.
The aim is not to crown a winner; it is to shorten the feedback loop so assumptions fail fast, fixes arrive sooner, and the entire ecosystem learns in public.
Bridging Quantum And Crypto Communities
Even the best algorithm falls flat when the two disciplines behind it speak different dialects. At IEEE Quantum Week 2024, more than 1,600 attendees from 44 countries joined workshops that paired quantum physicists with Web3 founders, according to IEEE. Yet many developers still say they struggle to “translate the math.”
That is where applied labs step in. We:
- Turn dense quantum-error-rate papers into threat models a smart-contract developer can paste into a GitHub issue.
- Brief quantum researchers on gas-fee economics and backward-compatibility headaches.
- Package findings in plain language that security teams, regulators, and investors can act on.
Making those bridges visible through joint hackathons, co-authored RFCs, and public threat briefings keeps quantum research from stalling in journals and moves it into wallets, nodes, and real-world defenses.
Why This Matters Beyond One Network
Bitcoin may grab the headlines, but the same quantum-fragile math supports much of the internet you use every day.
- Web payments. Visa estimates that 99 percent of its 257 billion annual card-present transactions travel over TLS channels still secured by RSA or P-256 ECDSA. Let’s Encrypt now protects 550 million sites, a 42 percent jump in 2024, yet most of those certificates would break under a cryptographically relevant quantum computer, the nonprofit reports.
- Identity and log-ins. Passkeys are growing quickly; Google counted more than 1 billion uses by 400 million accounts in 2024, according to The Verge. Yet many services still rely on classic FIDO U2F keys signed with ECDSA.
- Layer-2s and alt-chains. Networks such as Polygon, Optimism, and Solana rely on the same secp256k1 or Ed25519 curves that protect Bitcoin and Ethereum.
When one lab develops a tool for spotting exposed keys or guiding users through a post-quantum address swap, you gain a blueprint that migrates across payment rails, messaging apps, and even government ID systems. Quantum safety is not a single-chain upgrade; it is an internet-wide relay, and every reusable tactic moves the baton forward.
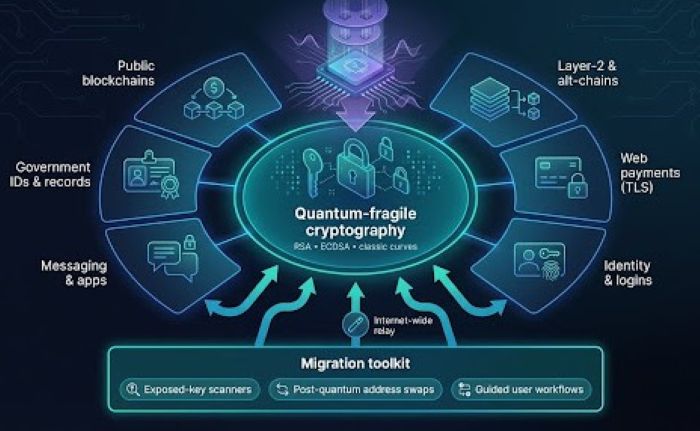
Quantum‑vulnerable cryptography underpins blockchains, web payments, identity, and more—making migration an internet‑wide relay.
How The Broader Ecosystem Can Help Defend Bitcoin
You don’t need a PhD in cryptography to make a difference and defend Bitcoin. In a 2025 Utimaco survey of 500 security leaders, only 20 percent said their organization has started migrating to post-quantum cryptography, while 25 percent admit they still have no plan at all, the company found. Closing that gap takes coordinated, practical steps:
- Ship safer defaults. As a developer, disable address reuse in your wallet or dApp and flag any spend that reveals a public key. Almost half of all crypto stolen in 2024 came from private-key compromises, accounting for 43.8 percent of the $2.2 billion lost, according to Chainalysis.
- Test migrations early. Custodians and hardware-wallet makers can partner with labs like Project 11 to run staged “sweep” drills on testnets long before a real quantum deadline forces emergency moves.
- Buy and fund readiness. Institutions can add post-quantum clauses to RFPs and allocate part of their security budgets to bug-bounty programs focused on PQC code.
Groups such as Project 11 accelerate that work by publishing open-source scanners, coordinating cross-vendor hackathons, and pushing new BIPs or EIPs that formalize quantum-safe migration paths. When you adopt or fund those tools, the industry shifts from awareness to measurable action.











